TL;DR
Today we are introducing AppTotal, the industry’s first publicly available community offering that automatically assesses the risks involved with OAuth apps. AppTotal builds on Canonic Security app sandboxing technology, dynamically scans SaaS add-ons for vulnerabilities and suspicious or malicious behavior.
SaaS-native integrations - third-party OAuth apps
I guess you’ve all seen this pop-up at least once and probably clicked allow too:
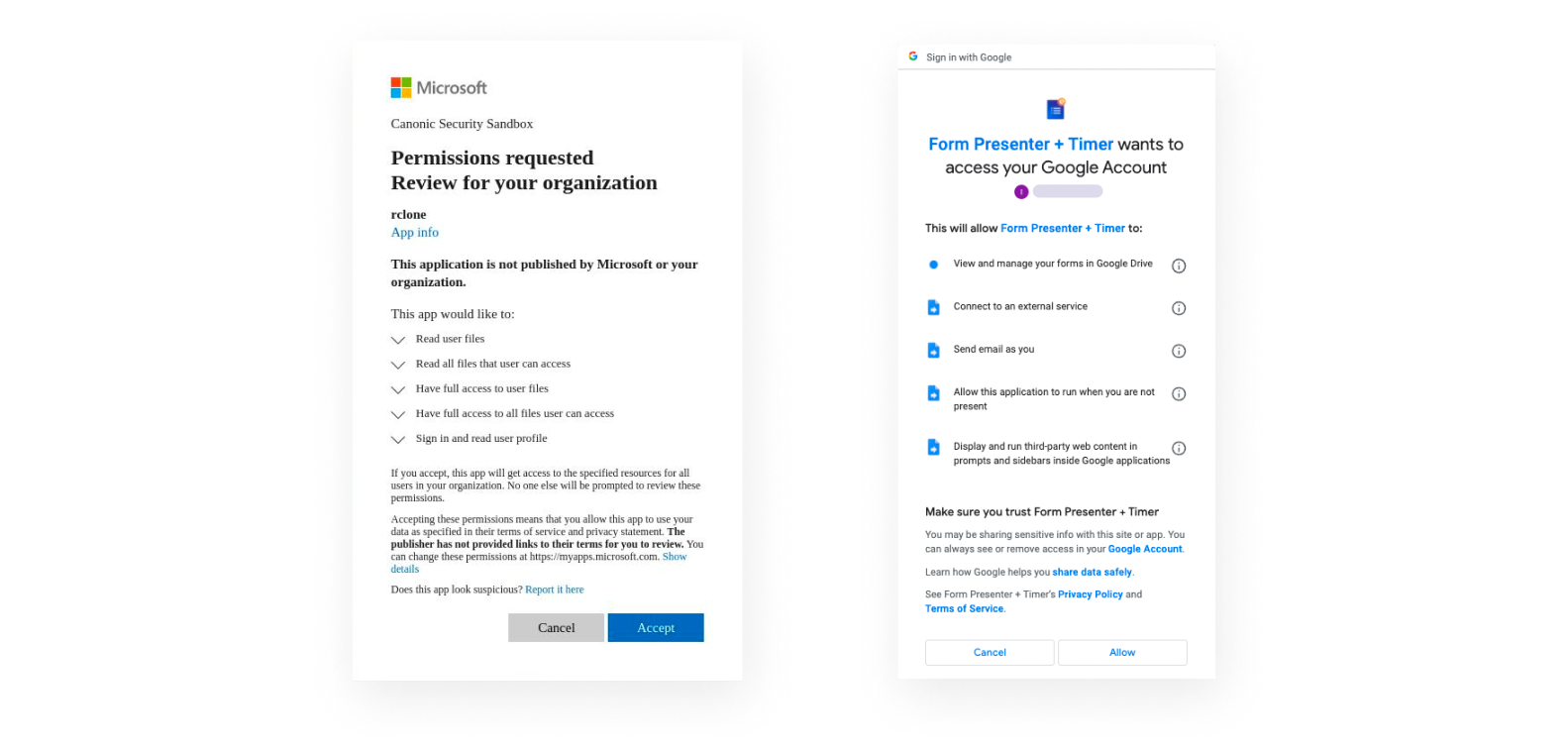
You probably got there from an email you’ve received, a marketplace app, a browser add-on, or as you casually signed in with your Google (or Slack, or Microsoft, or Facebook, or....) account to another SaaS service. But what do we actually know about these apps? what’s actually happening once you click allow? That’s the question I asked myself, so I dived into what type of attributes, activities, and meta-data we could actually extract for each OAuth integration, across different SaaS platforms, and the results weren’t promising...
Most platforms would hand out what’s required by the protocol: a clientID (which is a unique identifier of every OAuth application), an app name (Which is an arbitrary string, chosen by the app developer, when registering it with the platform), a developer identifier (maybe, these are vary by platform and are not part of the protocol itself), some kind of “verification” status (maybe, these vary by platform and who knows what’s the process behind them).
But once the app actually connects to the host platform, it behaves much like a binary running on an operating system — it has its “I/O” ops, it has its storage, it has its network ops, system calls (API calls here) — there’s some kind of execution flow. But how does that map onto SaaS platforms? Counterintuitively, wonderfully so. Although implementation and the amount of details you can actually extract varies widely.
So I figured, it might be kinda cool if anyone, could actually assess any app, before throwing it into their own environment, or investigate the attributes and behavior of an app already connected to their environment without researching OAuth app & platform internals manually... what if, just as one can submit a SHA/MD5 and see what AVs, Sandboxes and Threat intelligence providers have to say about it, one could submit an OAuth clientID?
The Challenge: Platforms vary, apps are many
It wasn't so easy. SaaS platforms (e.g., Google Workspace, Microsoft Azure) are not so upfront about third-party apps registered with them. What one would consider basic information, like vendor, publisher, description, etc — are often missing, plain incorrect, or unverifiable by nature of the platform and the protocol itself.
For example, in the tweet below, there is an OAuth app named "Email" (very indicative..), registered on Microsoft, with the publisher "Test". It has the client id, with vague information, so how we can determine if it's risky\malicious or legit?
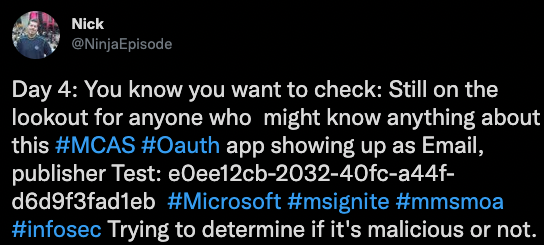
At Canonic Security, we actually focused on a slightly different use case at first — helping customers understand the risks involved with apps already connected to their SaaS environment: Once you have contextual information, risk “scores” are much more meaningful — a malicious app with Sign-in privileges may not be as dangerous as say, a vulnerable app with extensive drive/email access...
But revealing analyzing arbitrary OAuth client IDs, from the wild is a different ball game. We leveraged the knowledge we've gained while investigating our customer's environment and OAuth apps, utilized it to build collectors for the various platforms, and found ended up with some novel ways to tap into some of the missing information (which we may talk about later).
Did someone mention the first sandbox for SaaS apps?
The Solution: Introducing AppTotal Beta
AppTotal is the industry's first free community offering, letting anyone assess the risks involved with any SaaS integration, third-party app, or add-on.
Remember the "Email" app by the publisher "Test"?
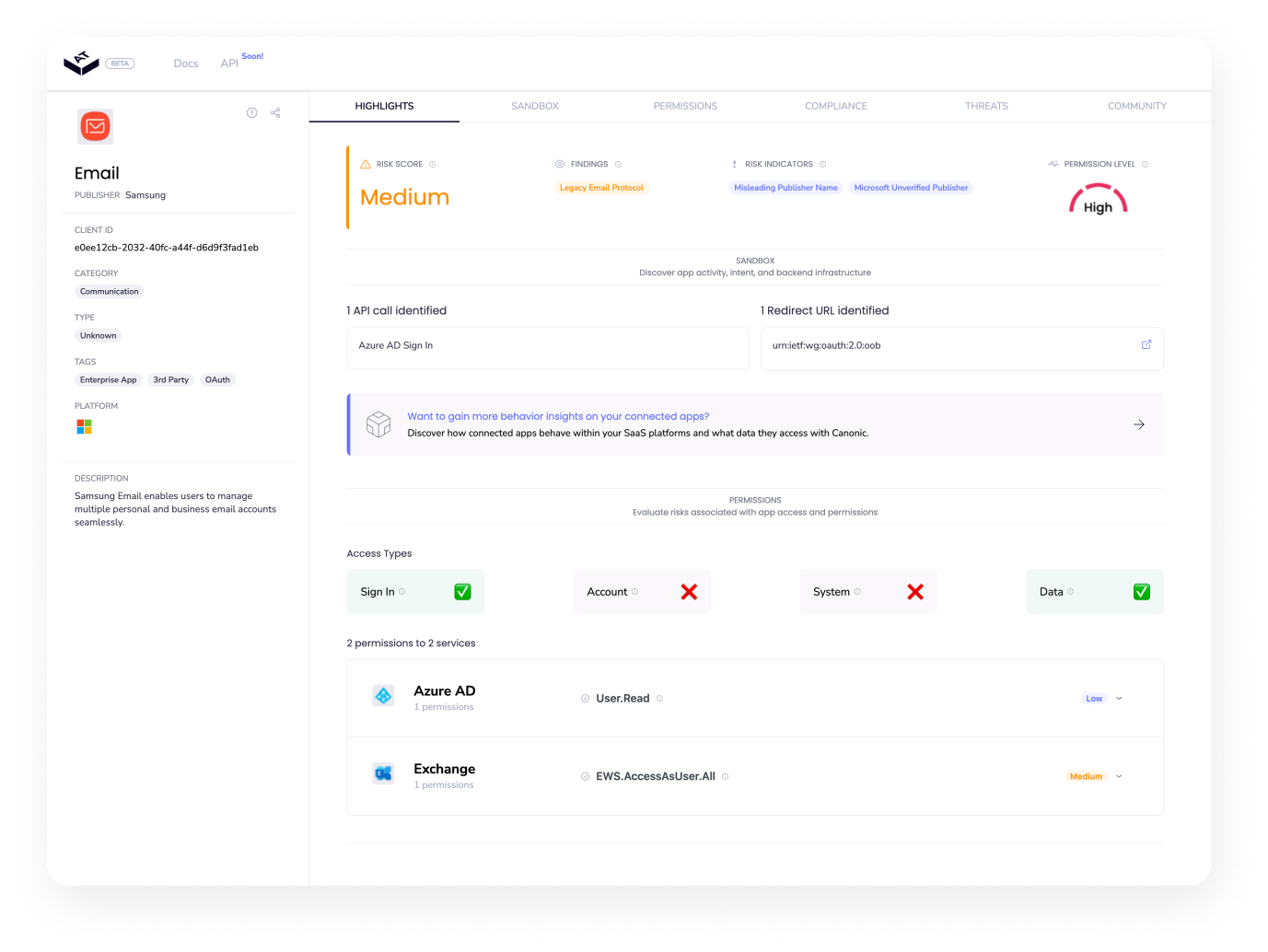
AppTotal lets organizations profile third-party apps' permissions and access, posture, and behavior before connecting them to IT-approved applications. It is the first independent and continuously updated SaaS add-ons and integrations index, starting with Google Workspace, Microsoft 365/Azure, and Slack, with Atlassian, Salesforce, and others coming soon.
With AppTotal, anyone can:
- Assess the risks involved with third-party apps before granting them access to your environment
- Uncover the app and publisher behind any OAuth client ID
- Analyze the behavior of third-party apps within your SaaS platform
AppTotal is a community tool, and we’d love to get your feedback and suggestions to support your SaaS security operations!



